No. The service adapts to businesses of all sizes. If your company handles valuable information (clients, finances, operations) or relies on technology to operate, it’s already vulnerable to attacks. Security Protect helps you stay protected, regardless of your size.
IKUSI CIBERSECURITY
IT Risk Prevention and Response for Organizational Assets
Advanced Services for Cybersecurity Companies
Tailored protection
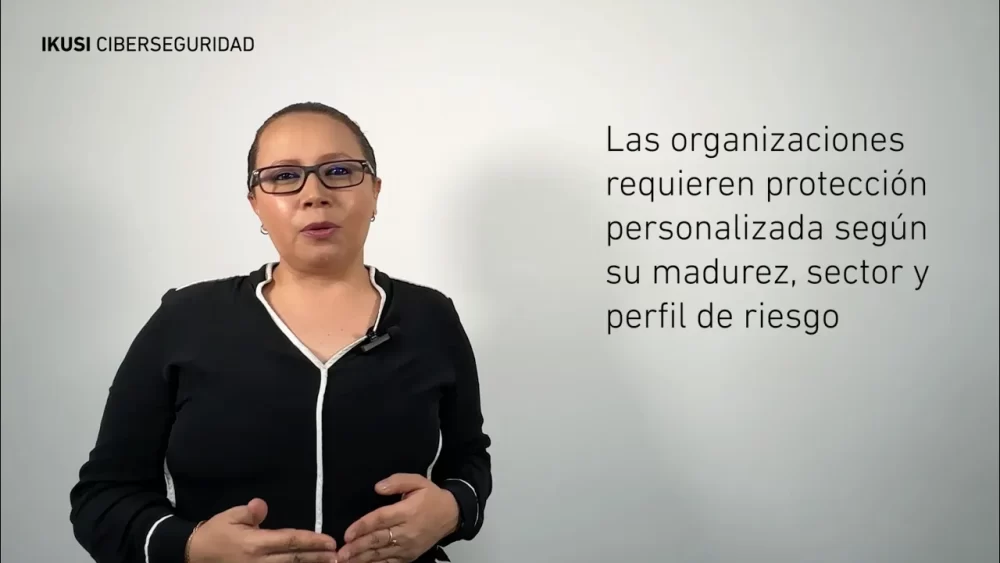
By tailoring the level of protection to each organization’s maturity, industry, and risk profile, it becomes a key solution for cybersecurity-driven companies seeking efficiency, automation, and full visibility.


Looking for a specialist in
IT Risk Prevention and Response
for Organizational Assets?
Envíanos tus datos y nos pondremos en contacto contigo para asesorarte.
Benefits
- Prevents operational disruptions caused by malware or ransomware
- Protects the network from unauthorized access and data theft
- Eliminates risks of impersonation and email fraud
- Analyzes and neutralizes threats in email attachments
- Keeps devices updated with the latest defenses, applying prioritized and timely security patches
- Provides consistent protection for remote users and headquarters
- Prevents leaks of confidential or regulated information
IT Risk Prevention and Response for Organizational Assets Solutions Applied to Today's World
Success Stories


Why Ikusi?
Our products and services involve personalized attention through our unified operations center, which provides proactive monitoring, support and management of network, cybersecurity and IT infrastructures.

Specialized Projects
At Ikusi, we deploy services and solutions to streamline operations, boost profitability, and enhance sustainability across multiple strategic sectors
The latest from our blog
Frequently Asked Questions
At Ikusi, we don’t just notify you. We provide clear, prioritized recommendations with the necessary context so you or your team can act quickly. You can also choose service models where Ikusi acts directly on your behalf.
Very little. Security Protect can operate remotely and adapts to your existing technology—servers, networks, email, etc. Only minimal integrations are required, guided by our experts.
You’ll receive monthly reports and have read-only real-time access to view activity. We also provide compliance indicators and clear trends that show the daily work being done.